OnionMail is an open source SMTP/POP3 compatible mail server with some functions designed for Tor hidden services. OnionMail use filesystem cryptography and some extended functions. This server also allows you to use the email in the tor network without losing the ability to communicate with the Internet.
«In the future, maybe we will implement the anonymous coffee!
Today, only OnionMail 😉 »
OnionMail functions:
- Multiple instances of server. (multiple indipendent hidden services).
- Native PGP integration for subscriprion and server`s message.
- Subscription via PGP encrypted email.
- VMAT Protocol (can use normal mail address without .onion).
- SSL cryptography by default. (STARTTLS 2048 bits)
- Multiple encryption everywhere, RSA + AES + RSA + AES with salt.
- Support unicode password (UTF-8 password and 2048 bits keyfiles).
- Inhibition of store any message in relay server.
(Only direct connection is allowed without multiple connections).- Metadata protection. NSA or GCHQ can’t read your metadata.
- SMTP Compatibility.
- Internet normal email compatibility.
- AntiSpam, blacklist and realtime filters.
- Decentralized trust system for SSL certificate and public keys and exit list.
- Native mailing list support.
- Garbage collector to remove automatically old messages.
- Clock and time zone spoofing.
- Server services and operations:
Add / Remove mail address or mail server in blacklist.
Mailing list Subscribe / Unsubscribe.
Request of server “rulez”. (Server help).
(All via mail message to the server directly “server@ xyz… .onion “)- JAVA Implementation for all platform.
- Native version compiled with GCJ.
- Localhost control port and server API.
- Protected server password and keys (optionaly not saved).
- IP BlackList
- Onion BlackList
- RSA Server and Tor connection authentication.
- Connections via Tor Network.
- Enter/Exit server to connect Tor to Internet and viceversa.
- Statistics in csv format.
- TorDNSLocalProxy to work with Exim4 and transprent SOCSK4A Tor Proxy.
- Strong cryptography (RSA 2048 bits, AES 256 + AES 256 + AES 256 ).
- Password key derivation via multiple keyfiles and passwords.
- Deleting files with wipe by default.
- Message headers filtering to hide informations and sigint.
- POP3 TLS Access.
- SMTP TLS Access.
- User’s parameters.
- Exit node selection to connect to internet.
- M.A.T. Protocol to connect correctly Internet, Tor, email and OnionMail.
- Server identification request via email to obtain the ssl certificate fingerprint.
- Self headers rebound to verifiy the client’s mail headers and OnionMail filtering.
- AntiSpam system.
- And much more…..
The real question is: «Why not???».
OnionMail defends the right to confidentiality of communications.
OnionMail prevents clandestine espionage “otherwise democratic” governments.
Usually other mail systems all mail messages pass through different SMTP servers often the connection is not encrypted.
With OnionMail the connection is always encrypted and the server does not saving data to disk. Only the recipient’s server stores the messages.The message files into the server are encrypted with asymmetric key, which is encrypted with the password of the user and the server keys. In the event of theft, the system does not reveal any sensitive data.
It always advisable to use PGP or GPG to encrypt e-mail messages.
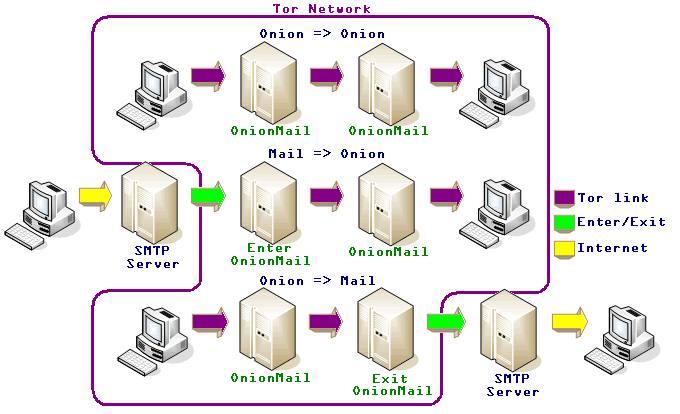
When a message is sent from the Internet it passes through the server Enter / Exit. These servers are the entry and exit nodes of Tor for e-mail. The user can choose which node to use to communicate to the internet.
Spam is short-lived because there are the custom blacklists. So each user can set their own spam filters.
All servers are federated to create a check system for SSL server certificates.
With systems like this X-Keyscore and similar technologies have big problems to intercept your mail messages.
- Messages with multiple recipients are allowed.
- There aren’t Delivery Status Notification. If there are any problems email client responds with an error directly.
- The message headers are filtered.
- The hostname and ip addresses in the mail headers will be deleted or replaced with [0.0.0.0].
- It compulsory to use TLS. (STARTTLS, SSL 2048 bits).
- You can manage the Blacklist and block individual addresses or entire hidden service to block spam.
- The messages are automatically deleted after a number of days even if unread.
- You can request services and information to the server by sending a message to the server@xy … z.onion
- Always follow the rules of the server. For more information please send a message with subject RULEZ to your server.
- The SysOp, admin or root user can’t read your private email messages.
- You can use anorma mail address via VMAT subscription to the exit/enter OnionMail server.
from here