VPN Gate Overview
VPN Gate Academic Experiment Project is an online service as an academic research at the Graduate School of University of Tsukuba, Japan. The purpose of this research is to expand the knowledge of “Global Distributed Public VPN Relay Servers” .
Why VPN Gate?
You can take three advantages if you use VPN Gate:
- You can bypass the government’s firewall to browse oversea web sites (e.g. YouTube).
- You can camouflage your IP address to hide the source of sending information over Internet.
- You can protect use of Wi-Fi with strong encryption.
Unlike existing VPN services, VPN Gate has strong resistance against firewalls.
VPN Gate is free of charge. No user registrations required.
VPN Gate Public VPN Relay Servers
There is a list of Public VPN Relay Servers on the VPN Gate Academic Project Web Site.
Anyone on the Internet can connect a VPN connection to any VPN servers on the list.
No user registrations are required.
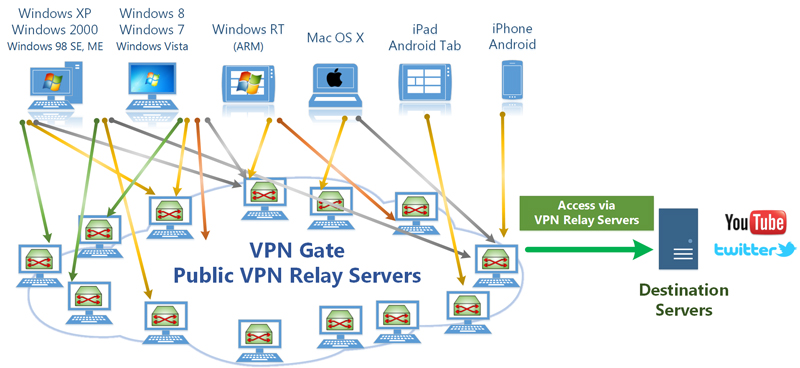
How does VPN Gate work?
- VPN Gate consists of many VPN servers, which are provided by volunteers around the world.
You can provide your own computer as a VPN server to join this experiment.
- Windows, Mac, iPhone, iPad and Android are supported.
- Supports SSL-VPN (SoftEther VPN) protocol, L2TP/IPsec protocol, OpenVPN protocol and Microsoft SSTP protocol.
- Anonymous connections are accepted.
- No user-registrations are required.
- IP addresses of each VPN server are not fixed. IP address may change at irregular period.
- VPN servers increase and decrease every day. Therefore, all VPN servers don’t located on the particular IP address range.
- While a VPN client is connecting to the VPN server, the VPN client can access to the Internet via that VPN server. You can hide your IP address of the client.
- When you use a VPN server which is physically located on an oversea country, your any communication are regarded as if it is initiated from that country. Then you can access to web sites, by using VPN Gate, which are usually unreachable from your country.
The problem that this research solves
Out motivation to begin the VPN Gate Experiment are to solve the following existing problems.
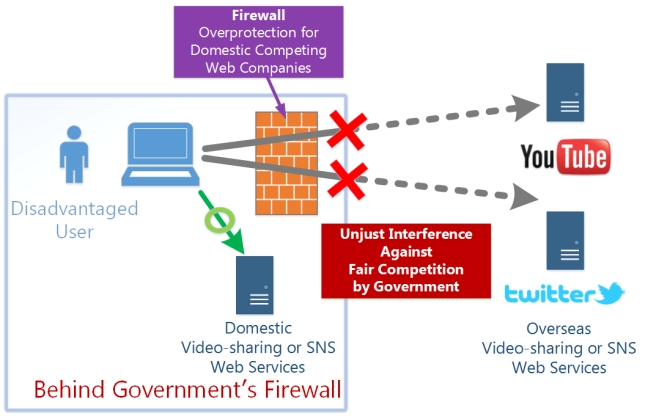
Existing Problem #1. Government’s Firewall Blocks to Access Oversea Web Services for Overprotection
The Internet is a revolutionary network to enable all user’s computers and servers to communicate each other without any restriction. Any web sites which are provided by individuals or companies can be reachable from anywhere around the world. Each people in the world is a potential customer of a web service. So every Internet companies are trying to develop and improve their web services continuously. World-wide competitions occur, and qualities of every services will be better and better, forever.
Such competitions over the world without any barriers are essential for improving the quality of Internet services. Internet provides such a great playing field for fair competition environment. However, some countries are attempting to interfere against the fair competition. For example, great video-sharing sites such as YouTube, or excellent SNS sites such as Twitter or Facebook, are existing in the world. Some governments place a contents-filter on the border between domestic and international Internet. Such a contents-filter is used to be called “Government’s Firewall” . People in such a country are often affected by the government’s firewall.
In United States, Japan and most of Europe countries, people prohibits their governments from placing such a government’s firewall, by the Constitution. However, it is said that some other countries have such a firewall for contents-filtering.
The government’s firewall force the people to use only domestic web services instead of international web services. They cannot visit international web-services which compete with domestic web-services. In other words, such a government supplies unfair advantages to the few domestic web-service providers in exchange for push inconveniences to the all Internet users of the country. In the long-term viewpoint such a government’s overprotecting policies will be cause of decline in public-interests, because most of people in the country are blinded to the world-valuable overseas web services.
It is convenient for users behind the government’s firewall if they can free-access to YouTube, Twitter, Facebook or other great web services. As the consequence, over-protected domestic web-service providers under unfair good-treatment by the government’s firewall will be involved to the world-wide fair competitions. In the long-term view, the competitions will improve both domestic and international web services, and every domestic people will receive benefits.
Existing Problem #2. Identifying an individual by tracing an IP address on the access log of the server is possible.
If you access to web sites, or send an e-mail, your source IP address will be logged on the destination web server, or on the headers included in the e-mail contents.
An IP address is not a personal information as only it. However, IP address can be used to track an individual who makes activities over several web sites. Such a tracing technique is used for unwanted advertising.
Additionally, an IP address can be used to identify the person who initiated the concerning communication, by using the law-enforcements procedures. Polices, prosecutors or lawyers can abuse their privileges to request the log files of IP address allocation which are hold by ISPs. Such IP address allocation logs are enclosed by ISPs in usual time. However, once someone obtains the logs, he can investigate who sent an e-mail, or who post a message to the web site. It might be abused to revenge to the one who conducted an indictment for public interests. The risk of IP address traceability might discourages the good people’s motivation to accuse something for public benefit.
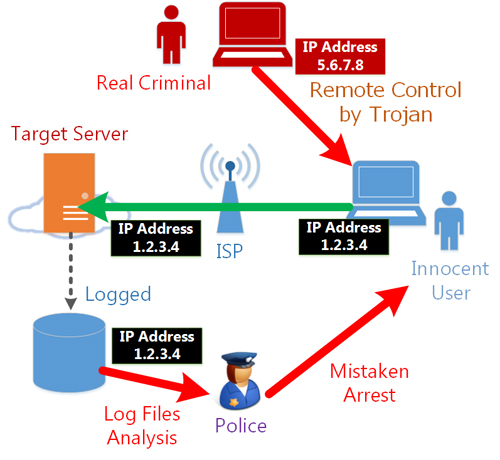
Moreover, on the Internet, a person who was assigned a specific IP address at a specific time will be regarded to have the responsibility of any illegal communications which were initiated from that IP address at the same time. Recently in Japan, law-enforcer’s disgraceful matters are criticized as serious problems that law-enforcement officers mistaken arrests innocent Internet users who never conduct nothing illegal on his computer but the computer was infected a Trojan which is controlled remotely by the real criminal person. The real criminal person let the computer of the innocent Internet user to send blackmails to some companies, and the innocent persons was arrested unjustly by law-enforcers. The innocents were finally released, but it was one of the worst false accusation incidents in Japan’s recent history.
Therefore, it is preferable that there is a method to hide your real IP address temporary when you access to the Internet. If your real IP address will be hidden, no advertisement-purposed IP address tracing will be unsuccessful. The risk of IP address traceability will be reduced, and the good people who are planning to accuse something for public interests will be easy to do it. The risk of mistaken arrests will never come to you if you hide your real IP address while connecting to the Internet, even if your computer is infected by Trojan or malicious software.
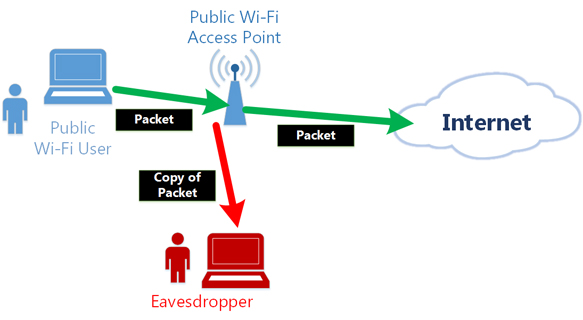
Existing Problem #3. Public Wi-Fi is under the risk of packet tapping.
Most of public Wi-Fi can be tapped by everyone. Your plaintext communication are not safe. Wired networks are also under the risk of tapping. ARP spoofing attackers can capture your packets. Moreover, the network administrator or the facility owner of cafe or airport who provides the public Wi-Fi can always tap on your communication. Even if you are using Internet at your home, there is a risk that the employee of your ISP or telecom company might tapping on the line to peek your plaintext packets. (In fact, there was a criminal incident that an employee of Nippon Telegraph and Telephone Company conducted the wiretapping in the telecom building. So we can never trust employees of ISPs or telecom companies.)
When using HTTP, POP3 or IMAP plain-text communication on the Internet, you cannot avoid the tapping. SSL (HTTPS) is secure against tapping, however most of web sites uses HTTP. HTTP packets are transmitted in the plaintext format.
It is preferable that there is a method to encrypt all communications to Internet servers automatically. In such a situation, no one on the local network or local telecom building cannot peek contents of your packets.
VPN encrypts and relays your packets
If you use VPN when you uses the Internet, you can solve above all of three problems.
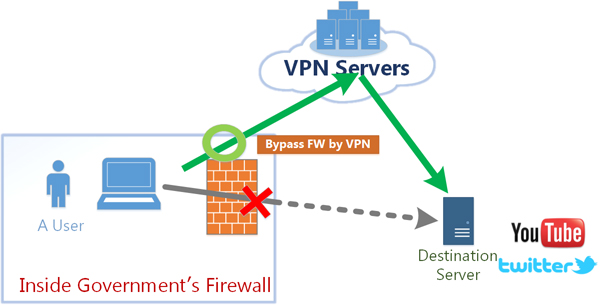
Solution 1. VPN can bypass the government’s firewall.
If the government’s firewall is out of order, and some overseas web sites are unreachable from behind the firewall, you can access such web sites via overseas VPN servers. The overseas VPN server will relay your communication towards the target web server.
Solution 2. VPN can hide your real IP address.
While the VPN connection is established, all communication’s source IP addresses will be replaced to the IP address of the relaying VPN server. This will very helpful for you because no one can no longer easily analyze and trace your real IP address of that moment. IP address logs on the target web server or the header list of e-mail will be recorded as if the communication was initiated by the relaying VPN servers. You can hide your IP address securely, and you can send anonymous posts or e-mails toward web sites or mail servers. It will encourages you if you are intend to conduct a righteous accusation for public benefits. You are now not under the risk of revenge by the accused person. Moreover, if your computer is infected by the Trojan which were sent by the “real criminal” , and the real criminal sends an remote operation to let your computer sends illegal blackmails to someone, you are no longer under the risk of mistaken arrests by law-enforcers.
Solution 3. VPN can prevent the tapping.
If you always use VPN, all communications will be automatically encrypted. Even if your neighbor on the local network is a wire tapper, your packets cannot be peeked by him.
Note that this solution can only encrypts the VPN tunnel, and can only avoid tapping on the local network. Packets between the relaying VPN server and the destination web servers are plaintexts. Plaintext packets might be tapped. However, at least local tapping can be prevented.
VPN Gate’s advantage to existing VPN services
As described above, VPN can solve several problems on using the Internet. However, usually you need at least one VPN server in the remote place (overseas) physically to exploit the functions of VPN as mentioned above.
Most of Internet users are unable to have their own VPN servers in an overseas country. For such users, there are existing paid shared-VPN services which are provided by some Internet companies. Such a service requires a user registration with credit-card number for payment, and an account will be created for the user. The user will gain the right of use the shared VPN servers for specific terms along to the contract.
So what is different between VPN Gate and existing such paid VPN services? In the viewpoint of users, the two seems to be similar. However, VPN Gate has differences to existing VPN services as described as following.
Problems of existing shared VPN services
Existing VPN services are implemented that the provider company hosts some VPN servers on the datacenter. This traditional way of providing some shared VPN servers on the datacenter has a problem that IP addresses of each VPN servers are on the same or similar IP address allocation block. Because the IP addresses are assigned by the same ISPs, generally. And IP addresses of each VPN servers are fixed, so they are seldom changed.
Such a shared VPN service has not tolerance against “unknown trouble on the government’s firewall” . The “unknown trouble on the government’s firewall” usually appears to the circumstance that some series of IP address blocks become completely unreachable from inside the country. If “unknown trouble” occurs to cover the IP address range of allocated IP address blocks for a shared-VPN server cluster, no VPN servers of the cluster will be unreachable from such a country. In fact, recently it is reported that one day a specific cluster of existing shared VPN servers become unreachable suddenly from a specific country which has the government’s firewall.
There is another problem of existing shared VPN services: occupation of bandwidth. Existing shared VPN servers are physically placed on the specific datacenter. All of every users’ communication will be concentrated at the Internet transit line of the datacenter’s uplink. And all processing workloads will be concentrated on some shared-VPN physical servers hosted in the datacenter. The service provider considers to increase the number of VPN servers in the cluster, or increase the bandwidth of Internet transit lines, but such expansions take costs. If cost increases, the fee of such a shared VPN service will increase. If serves cost, the speed of such a shared VPN service will be decline. Most of shared VPN services cannot provide the adequate quality to users.
Advantages of VPN Gate Academic Experiment
As you can see on the List of VPN Gate Public VPN Relay Servers, there are a lot of running VPN Gate Public VPN Relay Servers. These VPN servers are not physically placed on a specific datacenter nor a specific IP address allocation block; they are hosted on different ISPs and on physical locations to each other.
Every VPN Gate Public VPN Relay Servers are distributed and hosted by many volunteers. A volunteer is a person who owns a computer which is keeping the broadband connection to the Internet. He is a person who agrees to provide the CPU time and bandwidth to support the VPN Gate Academic Experiment. You can become a volunteer.
Volunteers are distributed geographically. The ISPs of volunteers are also distributed. So IP addresses of every VPN servers are distributed. No characteristics on the assigned IP addresses. The number of volunteers increases or decreases every day, and each IP address vary every time. If something “out-of-order” will occur on the government’s firewall, whole the VPN Gate Relay Server are not affected. If a few VPN servers become unreachable from your country, you can still reach other VPN servers.
Because VPN Gate servers are hosted by volunteers and each volunteer spends very small amount of costs for bandwidths and CPU times for his VPN server, the VPN Gate Service can be used for free of charge for everyone. The free of charge means that no user registration is required to anyone who wants to use VPN Gate service.
Therefore, unlike the existing shared VPN services, the VPN Gate Academic Experiment Service can be used with no paying.
Mirror servers of VPN Gate web site
Once a user connects a VPN session to one of the VPN Gate Public VPN Relay Servers, he can gain free access to the Internet from any country.
However, if the www.vpngate.net web site (this web site) is unreachable from his country, he cannot obtain the VPN Gate Public VPN Relay Servers List at first.
So we are providing Many Mirror Site URLs to help users who are in such countries. If a user can obtain access to at least one of the mirror sites, he can browse the VPN Gate Public VPN Relay Servers List page.
If you are a citizen of the country which has a government’s firewall with unknown error which prevents accesses to the www.vpngate.net from the domestic Internet, please access to the Mirror Sites List page, copy the URL list and paste it to SNS, Blogs or community forums in your country to help VPN users in your country.
VPN Gate is an extended plug-in for SoftEther VPN Software
Visit our another VPN project, “SoftEther Project”.
This is the parent project. VPN Gate is a child project of SoftEther Project.
from here